Security Considerations
VoiceCheck provides support for several methods of securing data communication. The following section shows how to configure the solution to use secure methods of transmission.
Options for Securing the Implementation
Voice Inspection Solution Security Options
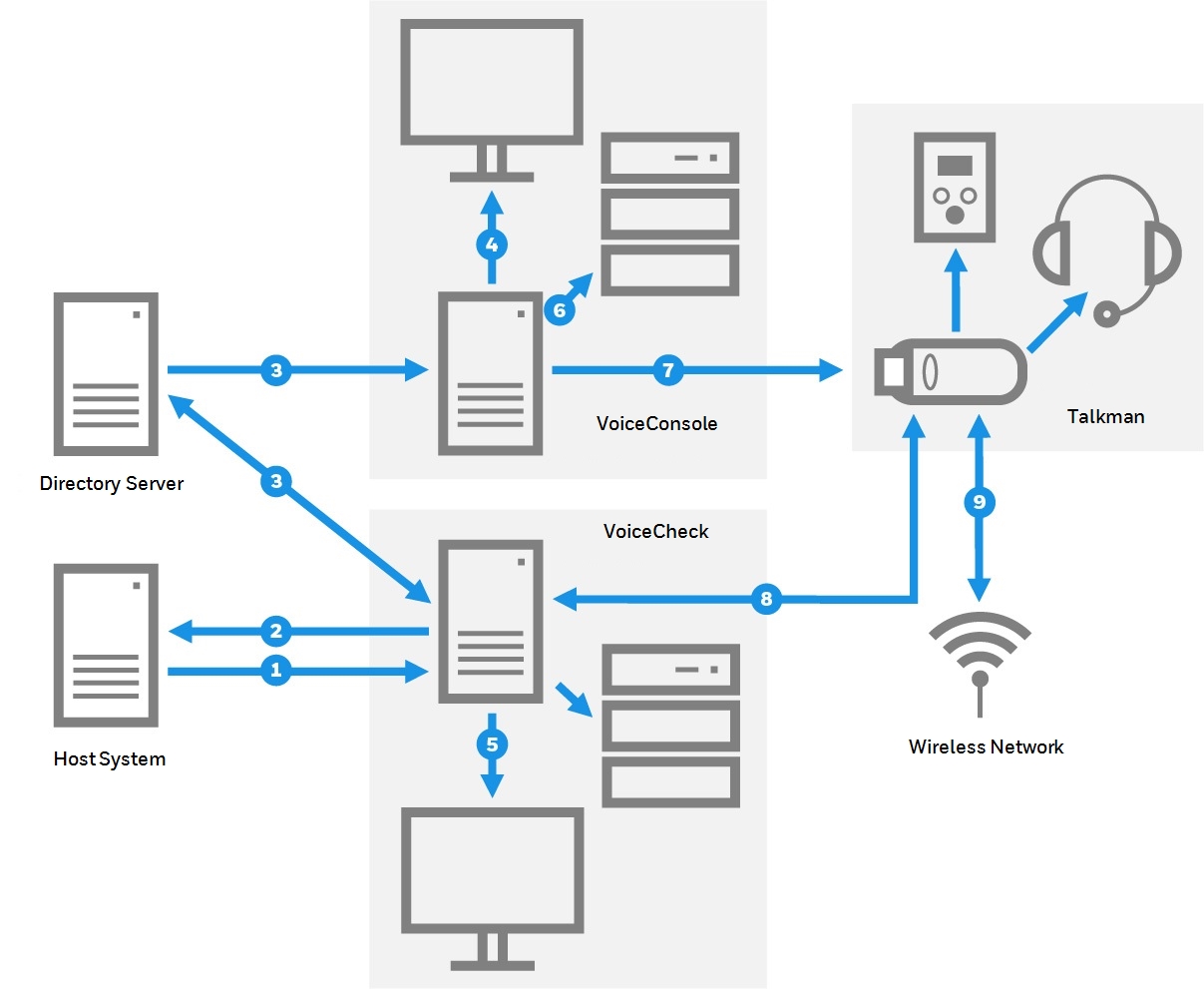
- Assignment import – an inbound web service transmission from the host system to VoiceCheck. Secure this data by configuring a server certificate on the VoiceCheck server and using an HTTPS inbound URL.
- Results export – an outbound web service transmission from VoiceCheck to the host system. Secure this data by configuring a server certificate on the host system and enabling HTTPS authentication in the Post Assignment Results Web Service Settings on the System Configuration page of the VoiceCheck GUI.
Results import – an inbound web service transmission from the host system toVoiceCheck. Secure this data by configuring a server certificate on the VoiceCheck server and using an HTTPS inbound URL. - User authentication – an option to use an existing directory server to authenticate VoiceConsole and VoiceCheck users. Set this option on the System Configuration pages of VoiceConsole and/or VoiceCheck.
- VoiceConsole web pages – the GUI pages served from Apache Tomcat to the client browser. Secure the web pages by selecting the Enable HTTPS Support option during the VoiceConsole installation and entering the certificate keystore information in the Tomcat configuration file.
- VoiceCheck web pages – the GUI pages served from Apache Tomcat to the client browser. Secure the web pages by selecting the Enable HTTPS Support option and entering the certificate keystore information during the VoiceCheck installation.
- VoiceConsole Embedded Database – a remote connection to an embedded database can be configured to use SSL (Secure Socket Layer) encryption. Secure this remote connection by installing a certificate and modifying a number of properties in the Apache Tomcat database.properties file. This option is not available for Microsoft SQL Server or Oracle databases and is not necessary for databases deployed on the same physical machine as the application server. See the VoiceConsole Implementation Guide for details.
- VoiceConsole device communications – wireless communications secured by WEP, WPA or WPA2 protocols, and data transmission from Talkman devices to VoiceConsole secured by HTTPS. Set both security options in Device Profiles in VoiceConsole.
- VoiceCheck device communications – data transmission between Talkman devices and VoiceCheck secured by Transport Layer Security (TLS/SSL) encryption. Install a certificate on the VoiceCheck application server, then select this option when creating a Task Package in VoiceConsole.Wireless network authentication – an option to deploy Extensible Authentication Protocol (EAP) to define data message formats for secure wireless communications among Honeywell solution components. Configure EAP on a site-wide basis by modifying the site in VoiceConsole.
Other communications shown in the graphic have security options that are not controlled within VoiceCheck. The VoiceCheck database should be deployed on the same physical network segment as the VoiceCheck application server, so wired network security can protect this data transmission as well as data sent between VoiceConsole and its local database. The Talkman device connects to a display device using HTTP and to SRX3 headset via Bluetooth v5.
Encryption and Authentication in VoiceConsole
VoiceConsole offers various options for securing the user interface, network communications, and device communications. Honeywell recommends combining encryption with a protocol that supports authentication methods to keep the networks secure.
- To secure web server communications, enable HTTPS during the installation, then obtain and install a certificate.
- To secure communication between VoiceConsole and Talkman devices, enable HTTPS in the device profile.
- To authenticate device connectivity on a wireless network, enable Extensible Authentication Protocol (EAP).
- To secure a wireless network with encryption, enable Wired Equivalent Privacy (WEP) or Wi-Fi Protected Access (WPA/PSK or WPA2/PSK).
- To verify users by authenticating logons against a directory service, enable LDAP support in System Configuration.
See the VoiceConsole Implementation Guide for more information.
Encryption and Authentication in VoiceCheck
VoiceCheck has secure options for data transmission between the application server and the user interface, the Talkman devices, and the host system.
- To secure web server communications, obtain and install a certificate, then enable HTTPS during the installation.
- To secure device communications, enable TLS/SSL in the task package.
- To secure access to a SOAP or REST web service on the host system for data exports, enable HTTPS basic authentication in System Configuration. The password is encrypted and stored in the VoiceCheck database.
- To verify users by authenticating logons against a directory service, enable LDAP support in System Configuration.
HTTPS and TLS/SSL
Hypertext Transfer Protocol Secure (HTTPS) is a networking protocol that secures web- or browser-based transactions over a network that is not secure. All HTTPS user connections are encrypted with digital certificates which tell the browser to use encryption to protect data transmissions.
This protection is effective only if the browser verifies a certificate as valid and issued by a trusted authority. Therefore, you must ensure that server certificates are installed correctly and the browsers used for VoiceConsole and VoiceCheck administration are configured to accept the certificates.
Transport Layer Security (TLS), commonly referred to as Secure Sockets Layer (SSL), is an encryption protocol that uses a public key infrastructure to secure data communications between a server and client. Like HTTPS, TLS/SSL requires that a certificate is installed on the server and a specific network port for secured transmissions to Talkman devices or a remote VoiceConsole embedded database.
If you are configuring the implementation for any of the HTTPS or SSL options, the following components are needed. See HTTPS Certificate Installation for more information.
- Java keytool utility to create a certificate request
- A signed certificate, that includes all intermediate certificates if any exist
Supported Authorities
Honeywell software supports the following certificate signing authorities.
- COMODO Certification Authority
- Cybertrust Educational CA
- DigiCert Global CA
- DigiCert High Assurance CA-3
- Entrust Certification Authority - L1B
- EssentialSSL CA
- GlobalSign Domain Validation CA
- GlobalSign Organization Validation CA
- Go Daddy Secure Certification Authority
- Microsoft Internet Authority
- Microsoft Secure Server Authority
- Network Solutions Certificate Authority
- Starfield Secure Certification Authority
- Thawte SGC CA
- VeriSign Class 3 Extended Validation SSL CA
- VeriSign Class 3 Extended Validation SSL SGC CA
- VeriSign Class 3 Secure Server CA
- VeriSign Class 3 Secure Server CA - G2
- www.verisign.com/CPS Incorp.by Ref. LIABILITY LTD.(c)97 VeriSign